In today’s API-driven world, Application security isn’t a nice-to-have—it’s foundational. Whether you’re building an enterprise-grade SaaS platform or a mobile app with social login, understanding how authentication, authorization, and identity work is essential for writing secure software.

Application Security Blog Series
This blog series is a hands-on guide to modern identity and access patterns. We’ll unravel standards like OAuth 2.0, OpenID Connect, and SAML; explore LDAP and Active Directory(AD); and take you behind the curtain with JWTs, PKCE, retry logic, and secure session handling.
To kick things off, here’s a high-level mind map of what we’ll explore in this Application Security Series.
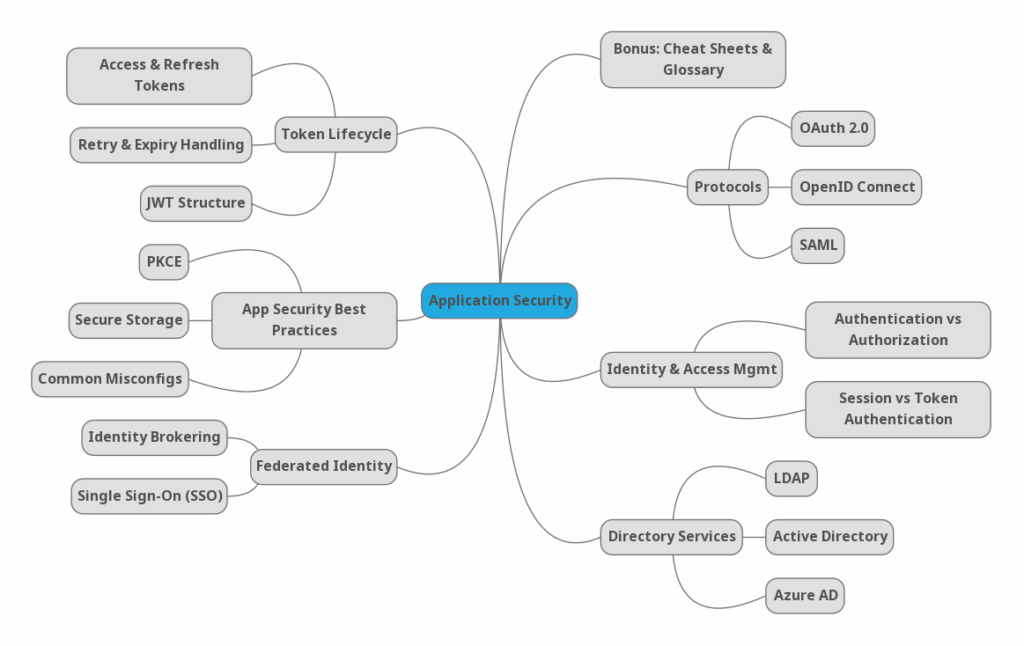
🛡 Upcoming Blogs in this Series 🛡
Part 1: Identity & Access Management
- Authentication vs Authorization: Understanding the Core Concepts of Modern Application Security
- How Session and Token Authentication Work (with Spring Security Examples)
Part 2: Security Standards
- OAuth 2.0 Deep Dive: A Guide to Tokens, Flows & Delegate Access with Spring Security
- OpenID Connect in Spring Security: Login, ID Tokens & Best Practices
- SAML Demystified: How Enterprise SSO Works (and When to Use It)
Part 3: Directory Services
- What is LDAP? A Developer’s Guide to Directory-Based Identity
- Active Directory vs Azure AD: Identity in the Microsoft Ecosystem
- Federated Identity Explained: Trust, Brokering & SSO Integration
Part 4: Token Lifecycle & Retry Logic
- Access Tokens, Refresh Tokens & Graceful Retry Strategies
- Inside JSON Web Tokens (JWT): Anatomy, Validation & Expiry Pitfalls
Part 5: App Security Best Practices
- PKCE and the Death of Implicit Flow: How to Secure SPAs & Mobile Apps
- Top OAuth/OIDC Misconfigurations and How to Avoid Them
Bonus
- SSO Deep Dive: How Seamless Login Works Across Platforms, Browsers & Identity Providers
- Backend for Frontend (BFF): A Safer Way to Handle OAuth Tokens in Modern Apps
- Application Security Glossary: A Developer-Friendly Guide to Auth, Tokens & Jargon
Who Should Follow This Series?
This series is designed to be both approachable and technically rich—packed with knowledge that will help anyone involved in building or scaling secure applications. Whether you’re just getting started or a seasoned expert, there’s something here for you.
- Software Architects crafting secure, scalable authentication flows in distributed or hybrid environments
- Application Developers implementing login systems or integrating with identity providers like Azure AD, Okta, or Google
- Security Engineers responsible for hardening authentication and access layers across platforms
- QA Engineers / Penetration Testers validating auth scenarios, token lifecycles, and SSO edge cases
- Product Owners & Tech Leads seeking to understand identity trade-offs that impact user experience and roadmap decisions
Further Links
- https://en.wikipedia.org/wiki/Application_security
- Check out our other Concepts category blogs. You will like them too.




